Do most breaches still occur through web applications? Let see how the security incident or breach played out last year. Actions that lead up to the breaches are stratified in Verizon’s 2022 Data Breach Report by the type of action and vector where the action was used to hack a system.
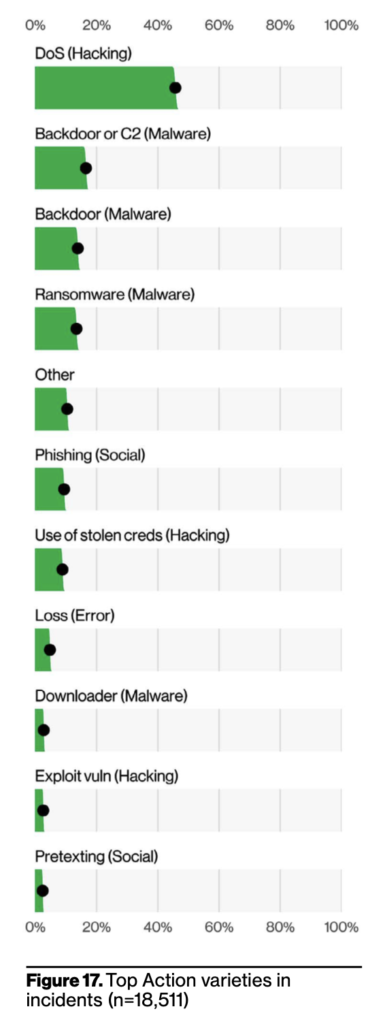
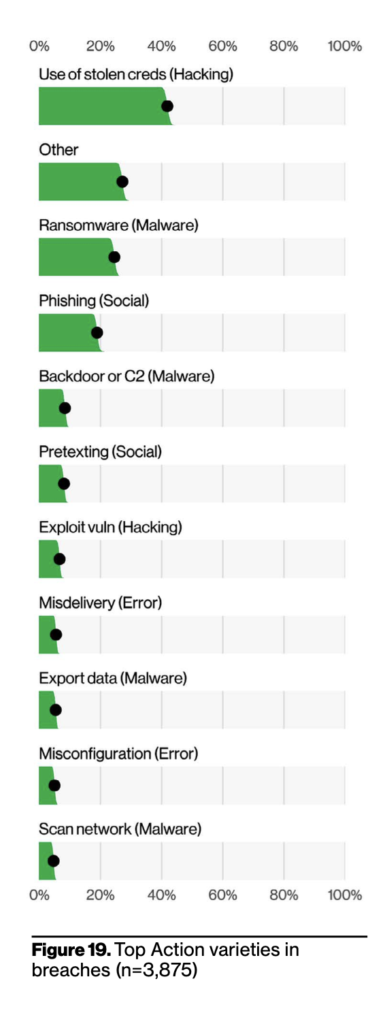
As you can see from the above two graphs, hackers used a lot of methods trying to breach (on the left). However the ones in the graph on the right turned out to be the most successful in actual breaches.
Same goes for the places that were initially breached by those methods. In the graphs below both attempted and successful breaches began with breaking into a Web Application of some kind.
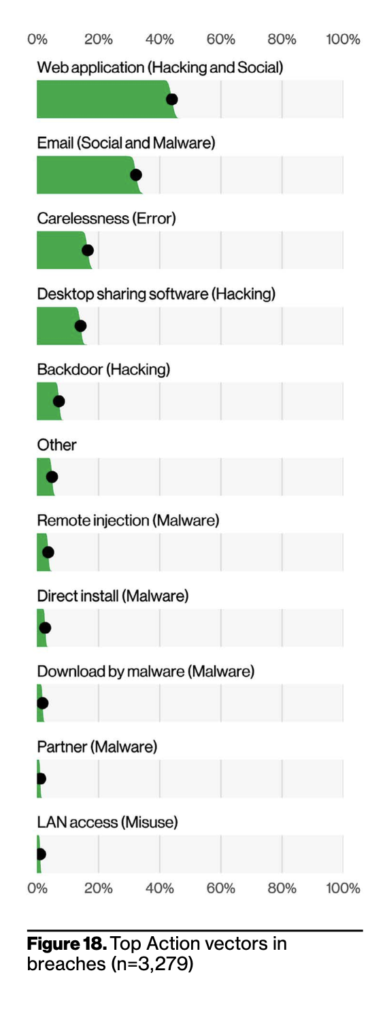
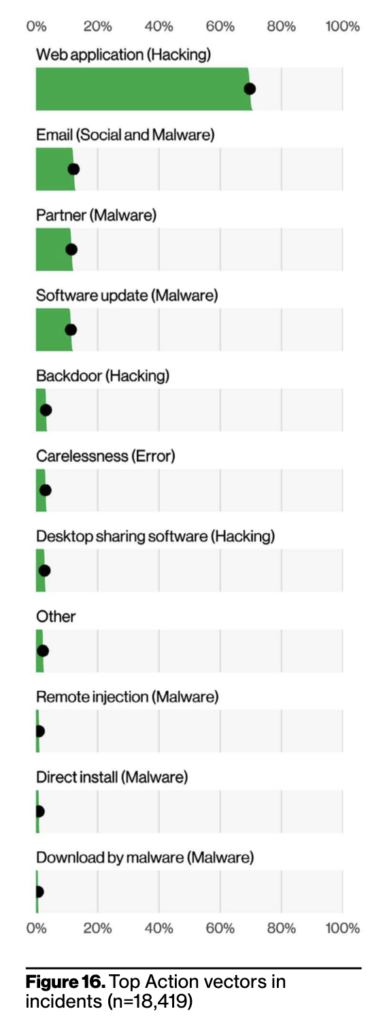
Web application is the number one vector, and, not surprisingly, is connected to the high number of DoS attacks. This pairing, along with the Use of stolen credentials (commonly targeting some form of Web application), is consistent with what we’ve seen for the past few years.
In terms of vectors, these align well with the notion that the main ways in which your business is exposed to the internet are the main ways that your business is exposed to the bad guys. Web application and Email are the top two vectors for breaches. This is followed by Carelessness, which is associated with Errors such as Misdelivery and Misconfiguration. Next we have Desktop Sharing Software, which captures things like Remote Desktop Protocol (RDP) and third-party software that allows users to remotely access another computer via the Internet. Unfortunately, if you can access the asset directly over the internet simply by entering the credentials, so can the criminals.
Glossary:
Hacking: attempts to intentionally access or harm information assets without (or exceeding) authorization by circumventing or thwarting logical security mechanisms.
Malware: any malicious software, script, or code run on a device that alters its state or function without the owner’s informed consent.
Error: anything done (or left undone) incorrectly or inadvertently
Social: employ deception, manipulation, intimidation, etc., to exploit the human element, or users, of information assets.
Misuse: use of entrusted organizational resources or privileges for any purpose or manner contrary to that which was intended.
Physical: deliberate threats that involve proximity, possession, or force.
Environmental: not only includes natural events such as earthquakes and floods, but also hazards associated with the immediate environment or infrastructure in which assets are located.
