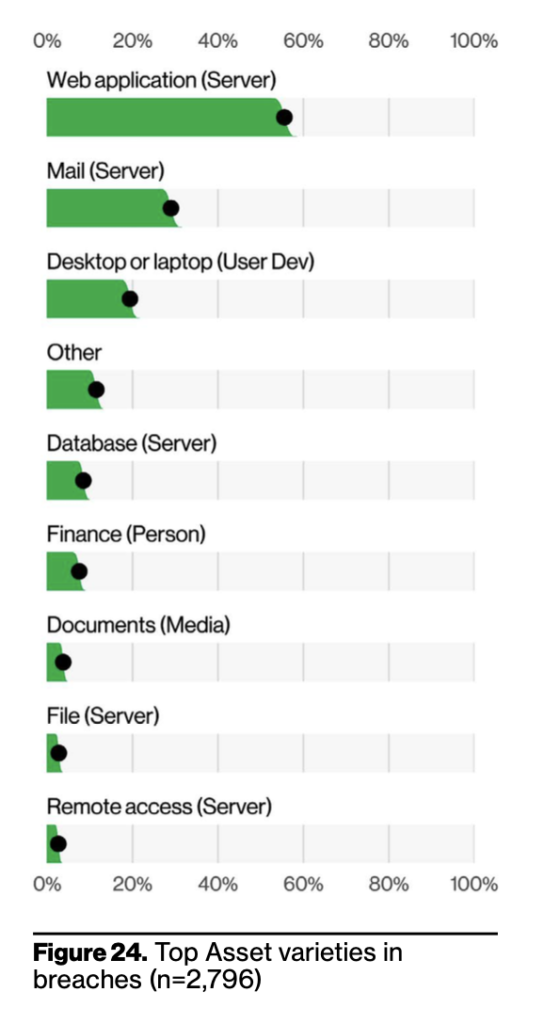
Assets are the things that you try to preserve. You can also find what was hacked via an exploit, and who was socially engineered by an attacker. This should help you understand what is being targeted and how to prioritize what type of coverage your infrastructure needs. Check out the specific types of servers on the graph. Web application (56%) and Mail (28%) servers are the top two varieties of assets. No surprise because email servers and web applications are the most likely to be internet-facing. Usually that’s the most comfortable for attackers who normally hack via the Internet.
While talking about of assets, we must remember that both IT assets and Operational Technology . Operational Technology computer systems run national infrastructures of the US and other countries . Those systems must be protected because they represent critical infrastructure.