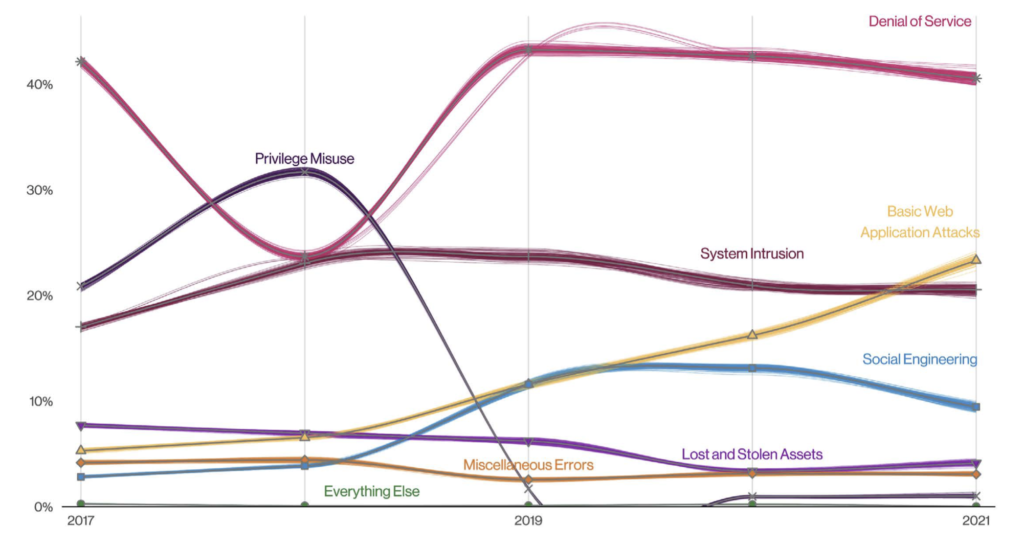
Patterns are essentially clusters of similar incidents. You can see there are eight patterns in this year’s Verizon report.
Basic Web Application Attacks
These attacks are against a Web application, and after initial compromise, they do not have a large number of additional Actions. It is the “get in, get the data and
get out” pattern.
Denial of Service
Attacks intended to compromise the availability of networks and systems. This includes both network and application layer attacks.
Lost and Stolen Assets
Incidents where an information asset went missing, whether through misplacement or malice.
Miscellaneous Errors
Incidents where unintentional actions directly compromised a security attribute of an information asset. This does not include lost devices, which are grouped with theft instead.
Privilege Misuse
Incidents predominantly driven by unapproved or malicious use of legitimate privileges.
Social Engineering
A psychological compromise of a person that alters their behavior into taking an action or breaching confidentiality.
System Intrusion
Complex attacks that leverage malware and/or hacking to achieve their objectives including deploying Ransomware.
Everything Else
This “pattern” isn’t really a pattern at all. Instead, it covers all incidents that don’t fit within the orderly confines of the other patterns. Like that container where you keep all the cables for electronics you don’t own anymore: Just in case.
